Now that we have the knowledge of what an NFT is, it’s time to learn more about the place in which they live: the blockchain. If we break down the name, we have two main concepts: blocks and chains (or links):
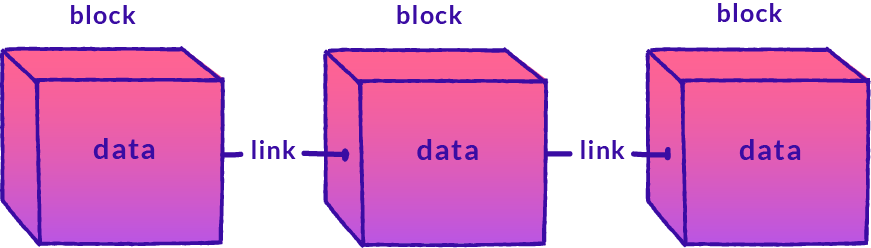
Block: Data consisting of transaction records and other blockchain-specific information. Each block is identified by a digital fingerprint called a Hash, a unique value that is a combination of new transaction data as well as data from previous blocks, to ensure connectivity and validity on the blockchain. The Hash can be thought of as a block’s unique ID.
Chain: Each one of those blocks also contains the previous block’s unique digital fingerprint, creating a chain of connected blocks that goes all the way back to the very first one. Because each block knows the previous block’s hash, it is very easy for anyone with network access to verify if someone has attempted to insert false data into the blockchain. This increases the overall security of the blockchain and helps ensure the blockchain can deliver on its promises of being a public, immutable transaction record that prevents double spending.
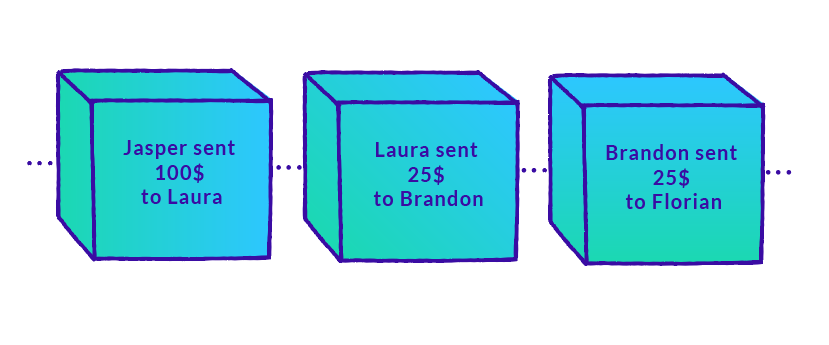
You can think of the blockchain as a public communal ledger that saves a set of records in the correct order. There is a large variety of transactions being recorded, from cryptocurrency being transferred to NFTs being minted, and it looks something like this:
Instead of having a ‘’main’’ instance, there are many copies of the blockchain that keep themselves up-to-date with each other by constantly syncing and ensuring all the information they share is consistent. That’s why blockchains are considered to be a distributed ledger.
Another key feature of the blockchain is that validated transactions are immutable (i.e. cannot be changed or reversed). Only new transactions can be added, meaning the history of every validated transaction remains intact.
Minting
Minting an NFT is the act of publishing that NFT on a blockchain.
When an NFT is minted or sold, it becomes one of a series of transactions that will be recorded and will live in that ledger book forever, as long as one of the peers maintains a copy of the ledger book publicly.
Each NFT retains a record of its transaction history: when it is minted, when it is sold, when it is sold for the second time, and so on. It looks something like this:

What gets written in the book is only the transaction, the code used to carry out the transaction, and a link or representation of the product. The book entry doesn’t contain the product itself in most cases, due to technical limitations of the blockchain. A good analog to this is property ownership: when you buy a house, you sign papers claiming ownership. These papers contain a description of the house, but does not in itself actually contain the house.
How a Blockchain Remains Synced
A blockchain is kept up to date by multiple different peers around the world cooperating to agree and validate the transactions before recording them in the shared ledgers. A peer in this context is not the average person transacting with currency, but a specialized ‘node’, or computer running software built to handle this specific situation. Peers are equal participants in the application, forming a network of shared resources, computational power and data storage. Typically, peers must have a rather high-end computer to handle all the computation required, and that’s only to post and verify transactions. Creation of new entries on a blockchain is usually beyond the capabilities of a single computer.
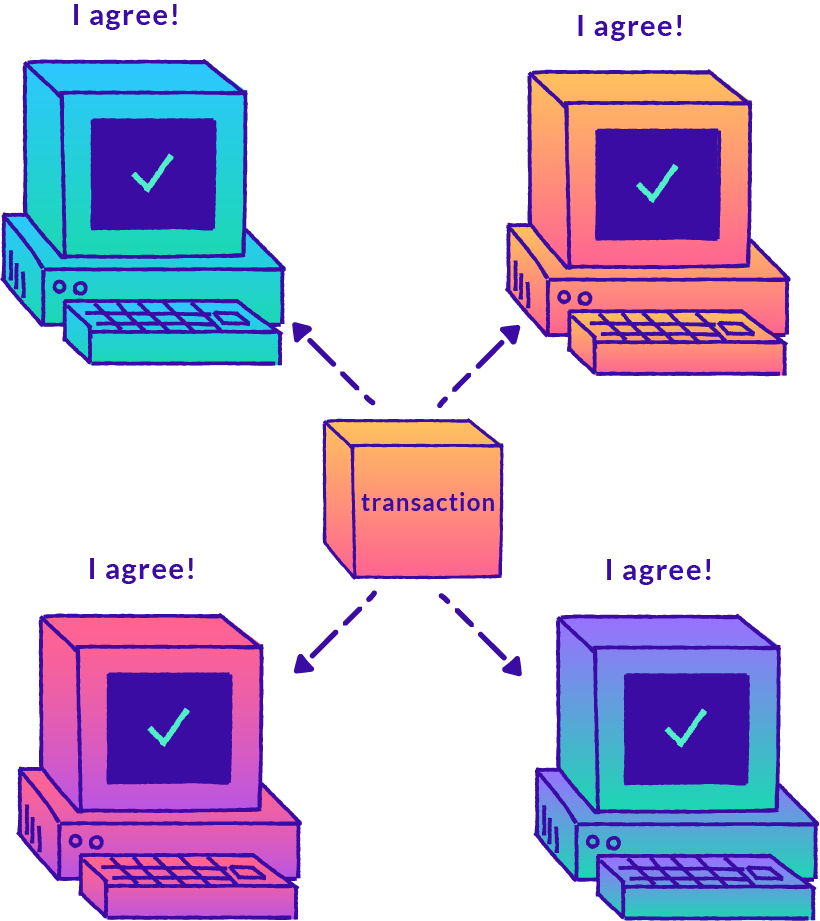
How Do Peers Reach Consensus?
After a list of transactions is recorded in a block, all peers need to agree on the validity of the transactions and also the order in which they were recorded. Once all peers have verified the validity of the block, consensus is reached, and all peers add that block to the end of their chain copies. Each time a new list of transactions gets created and validated, one of the peers will be the verifier and the others will be the proofers.
Every peer on the network has to be able to verify all transactions independently for any given transaction. This verification mechanism ensures a layer of security, ensuring validity of the transaction record and that no single user can manipulate it out of their own interests. These measures are in place to prevent double spending, a potential situation in which the same digital currency could be spent twice.
To this day there are two widely-adopted methods for establishing consensus on Blockchains: Proof of Work and Proof of Stake. Many more consensus mechanisms exist, but we won’t get into them here.
Proof of Work (PoW): In Proof of Work validation, after collecting enough transactions, miners race to create a valid block. For a block to be considered valid, it needs to solve a certain equation. This equation mixes the contents of the new block, its time of creation, the order of transactions, its link to the previous block in the chain, and other information.
This equation can’t be currently solved in any other way than just guessing the solution – a really big encrypted number – which requires a lot of time and energy. The miner who guesses the valid solution first is the verifier of that block, signing off on it. Correctness of this guess can be quickly verified by any other peer on the network. Blocks that don’t pass the validation are rejected.
Security in Proof of Work
By using a very difficult problem to solve, the system ensures that no single miner can find a pattern and start winning all the rounds (i.e. manipulate the results). In other words, fraud is, in theory, computationally infeasible. The incentive for solving these complex math problems, and thus spending large amounts of money on specialized machines and electricity, is to receive a certain amount of cryptocurrency for every block mined successfully. Security is also ensured by the fact a bad actor would need 51% of the entire network’s computational power (aka a lot of equipment and energy) to engage in malicious action.
Many miners in popular Proof of Work blockchains are members of mining pools – where members pool their resources to increase the probability of mining successfully. While individual users of these pools don’t have much power, the organizers of these pools, and thus the pools themselves, can disrupt a blockchain by determining what ends up on the blockchain and what doesn’t. This may result in a fork, a situation in which a network splits because parties can no longer reach a consensus.
Proof of Stake
Proof of Stake (PoS): Instead of having miners that compete against each other by solving complex math problems, Proof of Stake proposes that one peer, known as a validator, be selected at random to verify a given block of transactions. PoS networks do not use mining to validate blocks of transactions – they use what is called ‘staking’ instead. For a validator to be selected, they need to offer, or stake, something in collateral, typically a certain amount of that blockchain’s cryptocurrency. In Ethereum 2.0, a validator is required to have 32 ETH (at the time of writing ~ $93,000) to stake, at minimum – an expensive participation entry cost.
The more cryptocurrency staked, the higher odds of being selected as a validator. When a validator is chosen, they verify the validity of the block and share it with the entire network. Other users then double check the work of the validator. If the other validators approve it, the stake gets released and the winner earns fees associated with the transaction. This system has a feedback loop that favors users who can commit high stakes – making the highest stakers earn more rewards and so on, progressively increasing inequality and decreasing centralization over time.
Security in Proof of Stake
If a wrongful transaction is validated, or the chosen validator tries to manipulate the results in any way, the validator risks losing their stake. This punishment is the mechanism PoS uses to discourage malicious behavior. Security is also ensured by the fact a user would need 51% of the entire network’s coins (aka a lot of money) to manipulate results.
In short, PoW ensures consensus and security by making it too much work for bad actors to be able to act. On the other hand, PoS brings consensus and security by requiring parties to put down collateral, which they can lose if they behave maliciously.
While this is viewed by many as secure, it is still a risk because of stake pooling – i.e. when multiple stakeholders join efforts and resources to stake together and share rewards. This is a risk because multiple parties can collude together to take control of a majority of the currency. In fact, today four main pools control the majority of the Ethereum mining power and five mining pools control the majority of the Bitcoin mining.
1 This guessing game requires a LOT of computational power, and therefore consumes a large amount of electricity. This is exactly the point of the system – the underlying mechanism that makes it work. It is therefore a feature, not a bug, that PoW blockchains become more energy-intensive as time goes on. (source)(source)